Introduction
I know right, not too long ago you saw the wave of Web3 and now Web5? But stay with me.
Have you ever felt frustrated by the endless need to create a new profile every time you want to use a web application? Or you are tired of big corporations using or selling your data without your permission. Do you want to use a single identity(profile) to login to and use as many web applications as possible while having control over who should have access to your data, how long they should and revoke the access anytime you want? Let's talk Web5.
What is Web5?
Web5 is a decentralized category of web which give users ownership and control over their identity and data while interacting with Decentralized Applications (dApps). Decentralized applications are applications that are free from control or interference by a single authority or authorities. It make use of blockchain technology. In other words, Web5 provides you the leverage to have full autonomy over your identity and data. Alright, let's go into details.
You can have ownership and control over your identity by creating a globally unique username or Digital Identification (ID) which can be used to sign in easily across decentralized applications. Web5 gives you that benefit of using web services without having to create endless number of profiles. Also data such as name, email, phone numbers stays with you and you alone. Interesting, yeah?
You can also have ownership and control over your data by deciding who can have access to your data, how long they can have access to your data and revoke the access anytime you wish to. For instance, you can grant your doctor(s) access to your medical record(s) or you can grant your travel agent(s) access to your hotel reservations, meeting schedules and/or any data you wish to, perhaps for the purpose of serving you better . You also have control of how long they can have access to these data and revoke the access anytime you want to. This way, you won't be at the mercy of your service providers.
Team behind Web5
The creator of this revolutionary web technology is the former twitter CEO, Jack Dorsey, backed by a team at TBD, a bitcoin-focused division of his FinTech company Block (formerly known a Square). Web5 is a product of his concern about Web3 not being fully decentralized.
Pillars of Web5
Web5 is built on three pillars which are;
Decentralized Identifiers (DIDs)
Decentralized Web Nodes (DWN)
Verifiable Credentials
Decentralized Identifiers (DIDs)
Similar to Uniform Resource Locator (URLs), email addresses or social media handles people can use to identify and reach you or our organization, Decentralized Identifiers (DIDs) makes it easier to identify and locate you, your company or organization in the decentralized web. DIDs are unique identifiers which are made up of alphanumeric characters. Unlike your username or email which is tied to a specific service (@danieldunu on twitter), DIDs are not tied to a specific service as it can be used in all decentralized platforms.
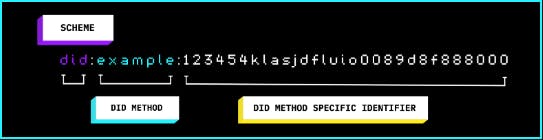
An image of a DID from the TBD website.
In the image above, you can see the DID method. DIDs have different methods. These includes:
did:key: These are DID methods which can only be created. These can be used in single exchange as it can't be updated or deleted.
did:ion: These are DID methods that not only can they be created, but also they can be updated or deleted. You can go as far as retrieving or deactivating a DID in this method.
DID Document functions as a storage for your DIDs. A DID document is a small JSON object that contains your DID in a field called id. Your DID can point to a DID document. This process is known as Resolving. This process allows you to search and get a DID document associated with a specific DID.
A DID also have a private-public key pairs. You should always keep your private key safe because that is a proof of ownership of your DID. You can keep your keys safe in a keystore.
Decentralized Web Nodes (DWNs)
We talked about having ownership of our data. But where is this data being stored? Decentralized Web Nodes (DWNs) are storage units where your data are stored and also being controlled by you. It is also a peer-to-peer relaying message network that is independent of any public blockchain.
This means it is responsible for receiving and transmitting messages, locating public or private data which you have given access to. All these can be done by resolving your DIDs and getting the address of DWN. These messages being transmitted are communications in JSON format which can include protocols, grant permissions, and read, create, update or delete a data.
You can host your DWNs anywhere and replicate them in different places across the decentralized web and all your data will be synced.
Protocol is a major feature of the DWN. It agrees on a mode of communication between two or more DWNs once it is installed in the DWNs. Protocols includes permissions and schema that enables two or more DWNs to communicate with one another.
There are three keys in a protocol document:
Types: It defines all components that is necessary in communicating between DWNS.
Structure: It houses the rules or permissions that governs each types in a protocol document.
Actions: These are rules or permission that governs the types. In the action, you can give permission to who can read or write a particular type. Example you can give give everybody permission to read your music playlist but only you can write(edit) the playlist.
Verifiable Credentials (VCs)
Much like identification methods such as Driver's Licence, Passports, Bachelor's Degrees, resumes and so many others, Verifiable Credentials (VCs) can be used as an identification method in Web5. VCs are digital credentials that allows you to show a particular section of your identity or qualifications without the need to pass through a central authority or reveal your whole identity. VCs are cryptographically signed.
VCs works on three-model structure: the Issuer, the Subject or Holder and the Verifier. Let's say you were a student of an institution. This institution (the Issuer), makes a claim about you being a student of their institution by signing your VCs with some cryptography. You (Subject or Holder), who the claim is being made about, can carry your VCs to be verified by anyone. Anyone can become the Verifier without the need for a middleman to confirm these claims. That's the interesting thing about VCs. Anybody can verify if you are an employee of an organization or a member of an institution without the need for an external agency to run background check.
As the Subject or Holder, you can share specific part of your employment history without having to share your whole employment history to the Verifier. Also these VCs are hard to forge as they are cryptographically signed by the issuer. Goodluck cracking the cryptography. It also eliminates the long processes or hours of waiting for your credentials to be verified by an external agency as the Verifier can verify on the spot.
These VC's can be safely stored in an identity wallet. You can retrieved them anytime the need for it arises.
How Web5 functions?
Web5 requires a Decentralized Web Platforms (DWP) to enable developers create Decentralized Web Apps (DWA) which run on peer-to-peer blockchain network using Decentralized Identifiers (DID) and Decentralized Web Nodes (DWN).
Relationship between Web2, Web3 and Web5.
Web2 is the centralized category of the web that involves participatory culture and encourages it's users to create content rather than just viewing them. We see that in blogs, social media and platforms where you can post, edit, like and even share. Examples are Twitter, Facebook, Instagram and various blogs.
Web3 on the other hand, is a decentralized category of the web which makes use of blockchain technology. It allows individuals have more control over their data.
Web5 is then the combination of Web2 centralized content platform like Twitter and Facebook and Web3 decentralized internet, powered by blockchain smart contracts. Put simply Web2 + Web3 = Web5. It doesn't seek to replace Web2 and Web3 entirely but rather to work with them.
Difference between Web5 and Web3
In as much as there are similarity between Web3 and Web5, you should also look at the dissimilarity between them.
Web5 has a lower barrier entry for creating applications while Web3 has a high barrier entry and often require specialized engineers for creating blockchain.
Web5 users store and control their data on a Decentralized Web Nodes (DWN) while Web3 stores their data on decentralized storages such a Interplanetary File System (IFS).
Web5 doesn't make use of tokens or smart contract while Web3 makes use of token and smart contracts to function.
Conclusions
With Web5, you can seamlessly interact with Decentralized Applications using a DID without creating multiple profile accounts for each applications. You can also grant service providers access to your data at your convenience while having control over how long they should have access to your data. You also have the power to revoke access to your data. For example, you can grant a medical app the permission to have access to your medical histories, for perhaps two months, to enable them serve you better. You can choose to revoke their access to your data when you want to.
With Web5, you have the privilege to avoid the stress of waiting for days or hours for an institution to verify your resume, Bachelor's degree or any credential. This is made possible by using your Web5's VCs. In an instance, the institution can verify the credentials you gave them access to.
This revolutionary web technology will give the users more power over their identity and data and enable them surf the internet seamlessly while being secured.
